As part of a week-long series focused on Mapping China’s Ambitions, The Cipher Brief is partnering with Harvard Research Fellow and former British diplomat Jamie Burnham to explore China’s threat vectors, how it is organizing to win, what a government ecosystem looks like and the impact that international collaboration will have in the future.
Today, Burnham focuses on the path toward a government eco-system. Earlier in The Cipher Brief, Burnham explored China’s broad ambitions and threat vectors, as well as how Beijing is organizing against those ambitions and threat vectors. So, once governments understand threats, how can they more effectively use their data?
Jamie Burnham, Research Fellow, Harvard Kennedy School’s Belfer Center for Science and International Affairs

Jamie Burnham is a research fellow at the Harvard Kennedy School’s Belfer Center for Science and International Affairs where he is exploring how digital technologies are changing political intelligence and policy-making. As a British diplomat, he served across Africa and the Middle East, with specific interests in weapons technology proliferation and the resilience of fragile states.
Knowledge is of no value if it is not used. A data analytics capability must act as part of a broader Government data eco-system. The UK’s integrated review of national security recognises that the state’s economic, security and influence capabilities can provide complementary advantage in achieving strategic goals. It recognizes that as the ‘volume of data grows exponentially, the ability to generate and use it to drive innovation will be a crucial enabler of strategic advantage.’
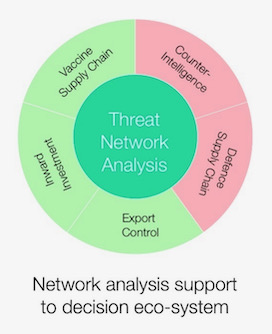
An analytics capability on China must be regarded as contributing insight and knowledge to policy and operational decisions across a range of security and intelligence functions. Core requirements might be, for example, providing information into low-side environments to enable early interventions in foreign direct investment decisions or export control orders or, perhaps, understanding the resilience of the vaccine supply chain. In a high-side environment, data can be fused with other collection systems to monitor impact on military capability or inform counter-intelligence investigations. Integrating data into a broader system is partly a technological challenge (using API gateways) but also demands collaboration across institutional boundaries to frame questions and build models.
Intelligence has long been provided in the form of reports: short, snappy statements that provide ministers and policymakers with timely insights into an adversary. Paper remains the basic unit of intelligence. However, different decision-makers consume data in different ways. A military commander, for example, will prize speed and accuracy of information in a tactical situation. While a defence minister will prefer the accessibility of a data dashboard to inform expenditure on new capabilities. In building information systems, the presentation and visualisation of data is as important a skill as the drafting of an intelligence report. The sorts of product that might be useful to government decision-makers might include:
- Investment Risk Assessment. A Cayman Islands-registered investment company seeks to take a shareholding in a British technology company. The government will want to understand the previous, known behaviour of the investment firm, its associations with the Chinese state and if the technology is a target for acquisition.
- Supply Chain Assessment. A vaccine manufacturing facility has a global network of suppliers. The British government wants to understand how dependent the supply of future vaccine is on the Chinese state.
- Overseas Intervention Support. The main shareholder of a British semi-conductor company is registered in Canada. A Chinese state-owned venture capital fund is seeking a majority stake in the Canadian owner. Transfer of the technology will support China’s military capability. The British diplomatic network requires information to support engagement with the Canadian government.
The Cipher Brief hosts private briefings with the world’s most experienced national and global security experts. Become a member today.
INTERVENTION AND DISRUPTION
The UK government is developing a range of policy responses that support improved national resilience, such as law governing inward investment. These will be necessary, but they are unlikely to be sufficient. Mitigating the risks of the behaviours exhibited by China may demand disruptive and targeted interventions that reduce adversarial effectiveness. These interventions may require the specific capabilities of the intelligence community or be overt. They must be legal, necessary and proportionate and subject to the oversight of ministers. They may include judicial or regulatory intervention or use of the global diplomatic network to enable action in overseas jurisdictions, for example collaboration with the US Treasury.
The impact may be increased if Chinese capabilities are thought of as networks, with interdependent nodes, rather than as stand-alone entities. The principles of network disruption are well established in countering military formations or terrorist networks but has not been applied to China’s acquisition capabilities. It requires an analytical approach which identifies the vulnerabilities in an adversary’s systems, against which limited resources can be focused. By analogy, a leader will seek to remove the queen bee from a hive rather than chasing thousands of worker bees. The RAND corporation’s ‘Vulnerability Assessment Method’ provides a useful template for structured analysis. It advocates use of the Carver principles to provide a numerical evaluation of different elements of a network.
Read part four of The Cipher Brief Special Series on China with Harvard Fellow Jamie Burnham in tomorrow’s Cipher Brief. You can catch Part One: Ambitions and Threat Vectors and Part Two: Toward a Government Data Ecosystem.
Read more expert-driven national security insights, analysis and perspective in The Cipher Brief
The post Mapping China by the Numbers: Toward a Government Data Ecosystem appeared first on The Cipher Brief.
from The Cipher Brief https://ift.tt/3uQ3CqK
via IFTTT
Comments
Post a Comment