As part of a week-long series focused on Mapping China’s Ambitions, The Cipher Brief is partnering with Harvard Research Fellow and former British diplomat Jamie Burnham to explore China’s threat vectors, how it is organizing to win, what a government ecosystem looks like and the impact that international collaboration will have in the future.
Yesterday in The Cipher Brief, Jamie explored China’s broad ambitions and threat vectors, today, he focuses on how Beijing is organizing against those ambitions and threat vectors.
Jamie Burnham, Research Fellow, Harvard Kennedy School’s Belfer Center for Science and International Affairs

Jamie Burnham is a research fellow at the Harvard Kennedy School’s Belfer Center for Science and International Affairs where he is exploring how digital technologies are changing political intelligence and policy-making. As a British diplomat, he served across Africa and the Middle East, with specific interests in weapons technology proliferation and the resilience of fragile states.
The government’s information architecture will have to be re-configured to meet the challenge posed by the Chinese state. Some of the policy responses are already maturing, most notably in the strengthening of the law governing commercial transactions in high priority technology sectors. The UK’s national security and investment bill introduces a hybrid system of mandatory and voluntary notifications on the grounds of national security. A more muscular application of existing tools such as export control orders is apparent. The Times newspaper reported that more than ‘200 UK citizens at more than a dozen universities’ were to receive export control enforcement notices. However, policy tools are ineffectual – and potentially damaging – if they are not supported by intelligence. Government requires timely insight in order to be less reactive, deliver earlier and less costly interventions, and exploit the global diplomatic and intelligence network to protect UK interests overseas. The modern data environment gives advantage to those who learn how to break down compartmentalized activity and share knowledge.
IDENTIFYING INTENT
The PRC’s intent in technology acquisition is well signalled. It is both strategic and pragmatic and rooted in historical behaviours. There is a long-term visible ‘desire to meet, by whatever means are necessary, the strategic goals of the time – whatever they may be – while at the same time building a system that can eventually self-perpetuate and be self-sufficient.’ Doctrine papers demand a whole of society approach to achieving a common aim. ‘Made in China 2025’, for example, seeks to upgrade Chinese industry so that it can occupy the highest parts of global supply chains and identifies ten priority sectors, including new advanced information technology; automated machine tools and robotics; aerospace and aeronautical equipment; maritime equipment and high technology shipping; modern rail transport equipment; new energy vehicles and equipment; power equipment; agricultural equipment; new materials and bio-pharma and advanced medical products.
While the broad outlines are clear, it requires more specialist skills and capabilities to identify the technology gaps that the PRC is targeting. Approaches might include:
- Technology baselines. Monitoring of academic publications and patents can establish progress in research fields. To achieve this, data analysts must collaborate with scientists to identify and understand the relevance of research papers. Academic thought leaders in high priority fields, such as quantum computing or biotechnology, can be identified and their academic collaborations mapped. Machine learning and natural language processing systems are required to do this at scale: the Chinese Knowledge Resource Database, for example, has over 71 million academic journals.
- Innovation Activity. It may be further possible to model which innovation centres, companies or state entities are commercialising new technologies and then map their relationships to external acquisition networks.
- Priority Metrics. Relative effort between technology fields to establish Chinese state priorities may also be quantified to establish relative effort and priorities.
- Information flow. The nature of Chinese technology acquisition requires priorities to be disseminated across a range of state and non-state actors, including NGOs and advocacy groups. Information may be sensitive, but it is hard to keep secret. It may be possible to model information flow and identify those nodes which reflect central intent. These networks are complex, and the information flow is often opaque, but government publications, tender documents, journals or speeches may provide indicators.
IDENTIFYING CAPABILITY
Technology acquisition networks are complex and diffuse. Relationships are often informal or opaque. It requires investigative techniques, combined with advanced analytical tooling, to identify the systems which pose risk. Established analytical approaches include:
- Risk Assessment. Analysts try and assess the risk posed by a person or a company to the transfer by looking at the behaviour of its broader network. For a person, risk flags might include the behaviour of associates or involvement with an NGO known to be active in technology acquisition. would involve arriving at a deeper understanding of the individual and broader association. For a commercial company, the analyst might look at its ultimate beneficial ownership, shareholders and employees. By characterising the behaviour of the broader network, and identifying any previous harmful activity, it is possible to come to an informed judgement about the risk posed.
- Network Discovery. Analysts need to hunt out unknown people or organisations which might pose a threat. Analysts first identify the sector they want to focus, for example quantum computing or biotechnology. They would then seek to identify those companies and academic institutions working in this area, for example through academic journals, corporate registries or government tender documents. The analyst would then determine the overseas footprint of those organisations by establishing its presence in overseas data holdings, for example corporate registries, or stock exchange filings.
- Automated Alerting. The scale of PRC activity is vast. Automated alerts can be developed which used pre-defined heuristics to identify suspicious entities, then present these as prioritised alerts for deeper investigation. There are two basic types of alerting. Firstly, developing a knowledge-base of known bad actors, then systematically washing this against datasets relating to a country’s key organisations, companies and institutions to identify matches. This can for example leverage fuzzy matching approaches. Secondly, looking for more sophisticated patterns indicative of suspicious activity, leveraging approaches such as machine learning. These more sophisticated approaches can take time to develop, leveraging the insight generated from entity-centric and top-down analysis to progressively build and iterate upon a set of rules over time.
AN EXAMPLE OF DATA MODELING
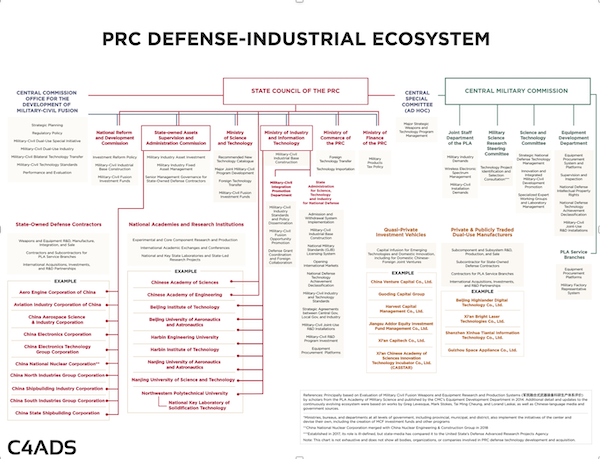
The Washington DC-based think-tank C4ADS has modelled PRC acquisition networks in the defence sector. This may provide a useful model for other technology areas. The doctrine of Military-Civil Fusion (MCF) under Xi Jinping has evolved long-standing concepts of military and civilian collaborative activity into a sophisticated eco-system. Commercial technologies are leveraged to develop military capability. The civilian industrial base participates in defence technology supply chains. Dedicated funds allocate capital for defence innovation. Conferences and trade fairs bring together defence contractors and dual use manufacturers. Industrial zones incubate new technologies.
C4ADS used data on PRC commercial and state organisations to identify four broad types of actor involved in overseas defence technology acquisition. A network diagram is at Figure 1. Using advanced data modelling techniques, they were able to identify:
- Contractors. 11 state-owned defence contractors such as the China National Nuclear Corporation and the China Electronics Technology Group dominate the defence industry. Between them, they control a network of over 800 subsidiaries and branch companies and are responsible for about 75 percent of the defence supply chain. All firms conduct business overseas.
- Investment Vehicles. A group of quasi-private six investment vehicles provide venture capital, private equity and incubator funds to the defence sector. These six companies own a further 232 companies, each investing in about 40 further businesses.
- Dual Use Manufacturers. Dual use manufacturers collaborate with state-owned defence contractors and sell directly to the PLA.
- Academic Institutions. A network of academic institutions support the PRC’s military R&D. The People’s Liberation Army (PLA) has established 43 universities and think tanks such as the Chinese Academy of Sciences. Other universities, such as the Seven Sons of National Defence, are integrated with State Library research hubs. Each university has its own corporate network which engages the international business community.
Having developed a model of defence acquisition networks, C4ADS were able to further illuminate their role in importing materials and technologies into the PRC. C4ADS was able to identify 65,272 incidents of imports to the PRC between 2014 and 2019. 61% of these imports were for potentially dual use goods, with the US, Japan, Germany and South Korea emerging as the top suppliers. Had it been possible to identify the materials as being associated with the defence sector, export control licences might have been applied.
The Cipher Brief hosts private briefings with the world’s most experienced national and global security experts. Become a member today.
ORGANISING TO WIN
To assume that ‘big data’ and AI will somehow easily meet your purpose, is to fail. The technology is not the challenge: organisational culture, fixed mental models and institutional boundaries are. Intelligence officers – whose lives are spent cloistered behind secretive walls – often struggle to comprehend that there might be information of value or interest in the real world. Shaped by the bitter truths of the Cold War, they have learned that knowledge hidden, is more advantageous than knowledge shared. In the world of hybrid competition, however, data is leaking across the matrix of globalised infrastructure. To ignore it, is to be blind. To isolate from networks that receive and share it, is to be deaf and dumb. Intelligence agencies may evolve into ‘knowledge platforms’ which collect information of value rather than sensitivity, and deploy skills in exploitation, analysis and delivery of impact.
SPONSORSHIP
Change within any organisation requires sponsorship. This is not simply a question of governance or budgeting. Developing an analytics eco-system, like other elements of government digital transformation, requires operating across institutional boundaries, building new operational models and challenging fixed assumptions. The urgency of crises and the need to deliver a succession of quick tactical fixes can preclude longer-term change within departments, allowing strategic debt to accumulate. The success of the UK’s Government Digital Service rested not just on the outstanding leadership of its founders, but the active support of Francis Maude, the Cabinet Office Minister. They recognised the need for a sponsor who understood the high costs of leaving the status quo alone. ‘Delivering change in the face of inertia takes a lot of time and energy as well as political capital.’ Any new capability must have the support of a senior leader who is personally committed to its success.
PEOPLE
People remain the most valuable ingredient. The skillsets required for data analysis are demanding. The UK government is blessed by analytical talent. Digital analysis, however, requires an evolution of the skillset. At the heart of analysis will remain the classic approaches demanded in making sense of complexity. David Omand terms these as the SEES: Situational awareness, Explanation of events and motivations, Estimates and forecasts, and Strategic notice of long-term strategic issues. Being able to frame the right question will always be hard – and the question will almost certainly have to be refined as the problem becomes better understood.
Digital analysis, however, poses additional challenges. Conventionally, analysts may determine patterns from established data sets, such as intelligence reports, media reporting or academic journals. However, the digital analyst faces the daunting task of searching for data in the infinite vastness of the internet, unclear about what to select or what patterns to look for. Each data set is likely to be of significant scale, have gaps and be structured uniquely. Above all, much of it is in a foreign language. There are plenty of pitfalls. Answers may look credible but in fact be wrong, perhaps because the wrong data was selected, or the cultural or linguistic context has been misunderstood, or the question was insufficiently defined.
Unpicking these challenges requires multi-disciplinary teams. A requirements specialist must engage with the broader government community to understand the policy or operational drivers and help frame the questions. Data scientists must develop statistical models and adapt analytical systems. Analysts must understand the context in which information sits and be able to interrogate it to find answers.
Organisational culture is fundamental to success. Assumptions must be challenged, and creativity and ingenuity applauded, if new pathways are to be discovered. Hierarchies must therefore be flat. A diversity of lived experience must be encouraged. No individual will arrive fully formed. People must be trained and mentored in order to flourish. Teams must be small in order to foster mutual trust and self-organize to find solutions. Individuals must develop broader social networks to leverage intellectual capital and fresh ideas.
TOOLS
The scale of data available and the challenge in making sense of it requires highly advanced analytical tools. The problems of large-scale data handling are not unique to government and the commercial sector is developing significant capabilities. Operating on the ‘low-side’ has costs associated with the procurement of new capabilities and infrastructure, but these are marginal compared to the challenges of in-house capability development necessary within in the intelligence community. The information architecture, and audit and security standards, may accord with commercial best practice. Indeed, one advantage of operating outside classified ‘high side’ systems is to trial new techniques and technologies, without risking compromise of secrets.
The systems should have the following characteristics:
- Powerful. They should be able to process and manage disparate data at large scale (billions of records), with the ability to apply updates as new data is received. They should be able to integrate advanced analytical technologies such as machine translation and natural language processing.
- Networked. They should empower technological and social collaboration, leveraging the insights of others within the UK and overseas, while providing data streams and intelligence products across government and to international partnerships.
- Knowledge-centric. Knowledge is accrued in two dimensions: time and place. Systems need to be able to build an archive of knowledge that becomes more useful exponentially over time. Relationships are drawn between people and organisations. They may only become apparent as more information is contributed. Different teams examining different domains need to be able to contribute elements to the same jigsaw, fitting things together that might not immediately be apparent.
- Collaborative. Government’s relationships with the commercial sector must change, from contractual to collaborative. Traditionally, desired functionality has been defined through an opaque requirements process, with budgets and timescales established more by auction than by understanding. The result is too often cost, delay and under-delivery. A mission partnership construct may permit the expertise and capabilities of state and private sector to be treated as complementary assets. By recognising that complex problems are solved through exploration and iteration, new business models will emerge which confer competitive advantage.
- Generative. By using unclassified data, innovation and the trialling of new techniques may be supported, for example using artificial intelligence for predictive modelling. These techniques may subsequently be deployed in other domains, for example defence or intelligence, with reduced risk and costs.
DATA
Traditional intelligence models place heavy focus on sensitive collection techniques, which are necessary but also slow and expensive. As information increases in availability and costs reduce, insight that was once the preserve of the state becomes readily available. The commercial world may watch North Korea’s nuclear programme from space or track mobile telephony. At the same time, maintaining secrecy becomes more demanding and more expensive. Data permits tracking of CIA spy aircraft in Iraq or Russian assassins in Salisbury. As publically available data becomes a tool of national security, it will itself evolve. Intelligence agencies, for example, will seek to conceal their activities by altering databases or by providing false information. Therefore the validation of data becomes a critical task.
In a ‘low-side’ domain, analysts may practise ‘data foraging’ by looking to the internet or commercial suppliers for valuable information. This provides the unique quality of speed. Commercial, academic and international partnerships may provide further data, analysis and techniques. An analytics capability should work to commercial norms and not seek data which is proprietary. Such data requires specific regulatory oversight and limits the dissemination (and therefore the impact) of information. Examples of the sorts of data that can be exploited include:
- Corporate registries and other datasets that describe corporate structure, investors, employees and ultimate beneficial
- Asset registries, e.g. property, vessels, aircraft.
- Tender data that details government contracts and opportunities.
- Academic papers, including journals, conference proceedings, details of masters and doctoral theses, lists of staff at institutions, awards for academic excellence and fellowship programmes.
- Trade data which includes the organisations involved in the transfer of goods, the nature of the shipment, and physical transport
- Financial records such as transactions and disclosures;
- Imagery derived from commercial satellite providers and social media.
Read part three of The Cipher Brief Special Series on China with Harvard Fellow Jamie Burnham in tomorrow’s Cipher Brief. You can catch Part One: Ambitions and Threat Vectors here.
Read more expert-driven national security insights, analysis and perspective in The Cipher Brief
The post Mapping China by the Numbers: Organizing to Win appeared first on The Cipher Brief.
from The Cipher Brief https://ift.tt/2TDza6n
via IFTTT
Comments
Post a Comment